Fortinet Threat Research Finds Cybercriminals Are Exploiting New Industry Vulnerabilities 43% Faster than 1H 2023
Fortinet® (NASDAQ: FTNT), the global cybersecurity leader driving the convergence of networking and security, today announced the release of the FortiGuard Labs 2H 2023 Global Threat Landscape Report. The latest semiannual report is a snapshot of the active threat landscape and highlights trends from July to December of 2023, including analysis on the speed with which cyber attackers are capitalizing on newly identified exploits from across the cybersecurity industry and the rise of targeted ransomware and wiper activity against the industrial and OT sector.
Key findings from the second half of 2023 include:
- Attacks started on average 4.76 days after new exploits were publicly disclosed: Like the 1H 2023 Global Threat Landscape Report, FortiGuard Labs sought to determine how long it takes for a vulnerability to move from initial release to exploitation, whether vulnerabilities with a high Exploit Prediction Scoring System (EPSS) score get exploited faster, and whether it could predict the average time-to-exploitation using EPSS data. Based on this analysis, the second half of 2023 saw attackers increase the speed with which they capitalized on newly publicized vulnerabilities (43% faster than 1H 2023). This shines a light on the need for vendors to dedicate themselves to internally discovering vulnerabilities and developing a patch before exploitation can occur (mitigate instances of 0-Day vulnerabilities). It also reinforces that vendors must proactively and transparently disclose vulnerabilities to customers to ensure they have the information needed to effectively protect their assets before cyber adversaries can exploit N-day vulnerabilities.
- Some N-Day vulnerabilities remain unpatched for 15+ years: It’s not just newly identified vulnerabilities that CISOs and security teams must worry about. Fortinet telemetry found that 41% of organizations detected exploits from signatures less than one month old and nearly every organization (98%) detected N-Day vulnerabilities that have existed for at least five years. FortiGuard Labs also continues to observe threat actors exploiting vulnerabilities that are more than 15 years old, reinforcing the need to remain vigilant about security hygiene and a continued prompt for organizations to act quickly through a consistent patching and updating program, employing best practices and guidance from organizations such as the Network Resilience Coalition to improve the overall security of networks.
- Less than 9% of all known endpoint vulnerabilities were targeted by attacks: In 2022, FortiGuard Labs introduced the concept of the “red zone,” which helps readers better understand how likely it is that threat actors will exploit specific vulnerabilities. To illustrate this point, the last three Global Threat Landscape Reports have looked at the total number of vulnerabilities targeting endpoints. In 2H 2023, research found that 0.7% of all CVEs observed on endpoints are actually under attack, revealing a much smaller active attack surface for security teams to focus on and prioritize remediation efforts.
- 44% of all ransomware and wiper samples targeted the industrial sectors: Across all of Fortinet’s sensors, ransomware detections dropped by 70% compared to the first half of 2023. The observed slowdown in ransomware over the last year can best be attributed to attackers shifting away from the traditional “spray and pray” strategy to more of a targeted approach, aimed largely at the energy, healthcare, manufacturing, transportation and logistics, and automotive industries.
- Botnets showed incredible resiliency, taking on average 85 days for command and control (C2) communications to cease after first detection: While bot traffic remained steady relative to the first half of 2023, FortiGuard Labs continued to see the more prominent botnets of the last few years, such as Gh0st, Mirai, and ZeroAccess, but three new botnets emerged in the second half of 2023, including: AndroxGh0st, Prometei, and DarkGate.
- 38 of the 143 advanced persistent threat (APT) groups listed by MITRE were observed to be active during 2H 2023: FortiRecon, Fortinet’s digital risk protection service, intelligence indicates that 38 of the 143 Groups that MITRE tracks were active in the 2H 2023. Of those, Lazarus Group, Kimusky, APT28, APT29, Andariel, and OilRig were the most active groups. Given the targeted nature and relatively short-lived campaigns of APT and nation-state cyber groups compared to the long life and drawn-out campaigns of cybercriminals, the evolution and volume of activity in this area is something FortiGuard Labs will be tracking on an ongoing basis.
Dark Web Discourse
The 2H 2023 Global Threat Landscape Report also includes findings from FortiRecon, which give a glimpse into the discourse between threat actors on dark web forums, marketplaces, Telegram channels, and other sources. Some of the findings include:
- Threat actors discussed targeting organizations within the finance industry most often, followed by the business services and education sectors.
- More than 3,000 data breaches were shared on prominent dark web forums.
- 221 vulnerabilities were actively discussed on the darknet, while 237 vulnerabilities were discussed on Telegram channels.
- Over 850,000 payment cards were advertised for sale.
Join the Discussion on Responsible, Radical Transparency at RSAC 2024
Learn more about the importance of driving responsible transparency across the cybersecurity industry from renowned industry experts during the session, “No More Secrets in Cybersecurity: Implementing Radical Transparency.”
Time: Thursday, May 9, from 10:50 to 11:40 a.m. PT
Location: Moscone South Room 156
Panelists:
- Carl Windsor, Sr. Vice President, Product Technology and Solutions, Fortinet
- Michael Daniel, President and Chief Executive Officer, Cyber Threat Alliance
- Eric Goldstein, Executive Assistant Director for Cybersecurity, DHS-CISA
- Suzanne Spaulding, Former Undersecretary, U.S. Department of Homeland Security
Turning the Tide Against Cybercrime
With the attack surface constantly expanding and an industrywide cybersecurity skills shortage, it’s more challenging than ever for businesses to properly manage complex infrastructure composed of disparate solutions, let alone keep pace with the volume of alerts from point products and the diverse tactics, techniques, and procedures threat actors leverage to compromise their victims.
Turning the tide against cybercrime requires a culture of collaboration, transparency, and accountability on a larger scale than from just individual organizations in the cybersecurity space. Every organization has a place in the chain of disruption against cyberthreats. Collaboration with high-profile, well-respected organizations from both the public and private sectors, including CERTs, government entities, and academia, is a fundamental aspect of Fortinet’s commitment to enhance cyber resilience globally.
It’s through constant technology innovation and collaboration across industries and working groups, such as Cyber Threat Alliance, Network Resilience Coalition, Interpol, the World Economic Forum (WEF) Partnership Against Cybercrime, and WEF Cybercrime Atlas, that will collectively improve protections and aid in the fight against cybercrime globally.






















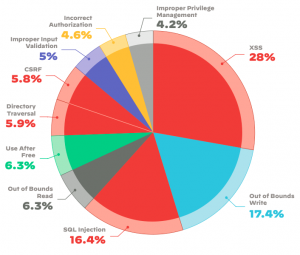 I wrote my first story about the perils of SQL injection more than 20 years ago, and even demonstrated how anyone using a simple Google search could pull this off. Sadly, things haven’t changed. Unit42’s report found these two old chestnuts are still ranked in the top three most disclosed types of vulnerabilities in their report.
I wrote my first story about the perils of SQL injection more than 20 years ago, and even demonstrated how anyone using a simple Google search could pull this off. Sadly, things haven’t changed. Unit42’s report found these two old chestnuts are still ranked in the top three most disclosed types of vulnerabilities in their report.